Let’s start by explaining what is a Virtual Private Network and which kind of VPNs we can find.
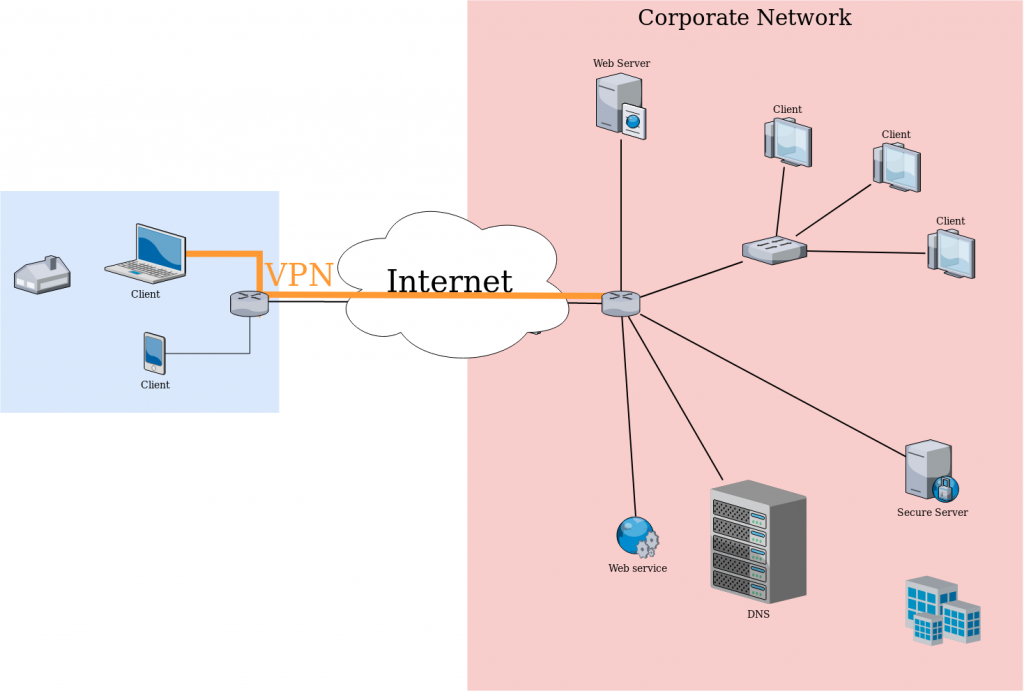
Corporate usage of a VPN
A VPN is a private connection to a network, if we look at the above diagram we can understand it better. We can find mainly two different uses of a VPN:
Corporate use : The connection between a device that is not in our network and our network will go through the internet. This means that all the resources that we have in our network won’t be able to be accessed unless we allow them to reach internet. But when using a VPN our remote device will have a “tunneled” connection to our network. We can look at it as a virtual Ethernet cable that will plug our device from wherever it is to our private network. This is the case ilustrated in the above diagram.
This can have several benefits, as we avoid our private services to be accessed from internet the private network can be better isolated avoiding possible security breaches. In this case we will need a device in our private network that will act as a gateway for the remote devices.
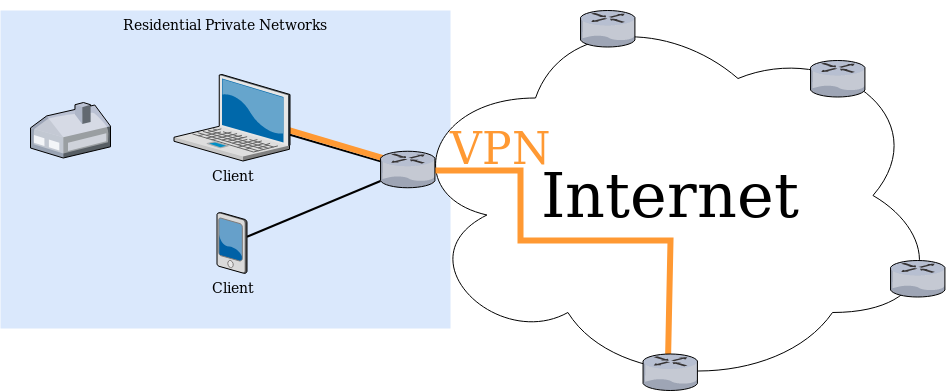
VPN for privacy diagram
Privacy use: Some people also uses VPN to anonymize their traffic. Using a VPN to anonymize the traffic can be helpful for instance if we want to access content that is blocked by region. Connecting to a VPN that may allow us to create a tunnel to a device in another country enabling the device to access that blocked content. Some people is concerned about the data collection that some companies as Google or your Internet Service Provider can collect about us.
For this cases we can usually use a third party VPN service that will allow the end devices to have an encrypted connection to any of the third party company endpoints. This protects the connection from our device from being traced for companies that route our traffic from our device to the VPN endpoint. As the end-point will be used by several clients at same time will be hard to trace any IP traffic. (This does not mean that the connection is not traceable, sessions with different services will still be established, and therefore trace the end device. But will block most Internet Service Providers (ISP) from logging and profiling connections.)
Once explained the top 2 uses of VPNs let’s see technically the 2 most deployed solutions for establishing a VPN:
IPSec Tunnel: When using IPSec there are several different protocols that can be used to create the secure connection. The key of IPSec VPN is the fact that operates at layer 3 in the OSI model. This is the IP layer, this means that the remote device is going to be virtually in the same network as the VPN server, or in a network that the VPN server is configured to be endpoint or relay. Usually the VPN server is the same firewall.
SSL tunnel: This kind of connection acts in the layer 4 to 7 in the OSI layer. This layer are the session and application layer, meaning the tunnel is created by each connection or in a whole application. In this type of VPN we can find more granularity in the control which means more detailed security profiles can be applied. Nevertheless the management effort that this granularity can generate is as complex as the access control that we want to implement. This type of VPN is usually served from a particular server inside the private network, meaning behind the firewall.
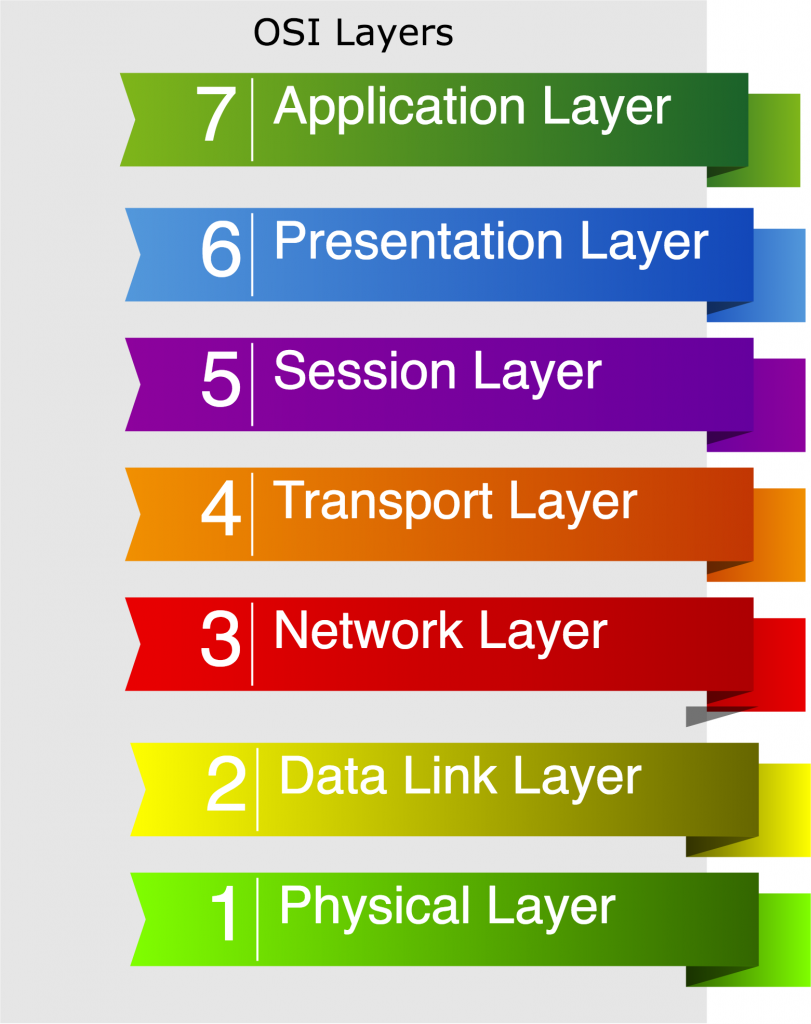
A great advantage that we can find in SSL VPNs is the fact that does not require a host level connection, the tunnel can be created at the application layer. This is an advantage because you can use a lightweight app client.
The best VPN for you really depends on each particular projects and there are several parameters that must be considered when taking the decision, we consider that the most basic approach must consider at least the following two:
-Security level (Who is going to connect, are the remote endpoints secure, …)
-There is enough bandwidth to handle all the endpoints traffic or make more sense to only send the traffic of specific application trough the VPN.